OWASP Juice Shop
Probably the most modern and sophisticated insecure web application

https://owasp-juice.shop
Björn Kimminich | @bkimminich | infosec.exchange/@bkimminich | @bkimminich.bsky.socialWhat is "OWASP"?!?
The Open Worldwide Application Security Project® (OWASP) is a nonprofit foundation that works to improve the security of software. Through community-led open source software projects, hundreds of local chapters worldwide, tens of thousands of members, and leading educational and training conferences, the OWASP Foundation is the source for developers and technologists to secure the web.
Open Worldwide Application Security Project and OWASP are registered trademarks of the OWASP Foundation, Inc.
Why "Juice Shop"?!?
Translating "dump" or "useless outfit" into German yields "Saftladen" which is a compound word from "Saft" and "Laden". This reverse-translates into "juice" and "shop". Hence the project name.
That the initials "JS" match with those of "JavaScript" was purely coincidental!
Customer Testimonials
The most trustworthy online shop out there (@dschadow)
The best juice shop on the whole internet! (@shehackspurple)
Actually the most bug-free vulnerable application in existence! (@vanderaj)
First you 😂😂 then you 😢 (@kramse)
But this doesn't have anything to do with juice (@coderPatros' wife)
Juice Shop Project Leaders
| Björn Kimminich | Jannik Hollenbach |
| 🏆WASPY Award 2021 "Outstanding Innovator" |
🏆WASPY Award 2025 "Project Person of the Year" |
Click here for a happy path shopping tour!
Unsuspectingly browse the Juice Shop like Average Joe!
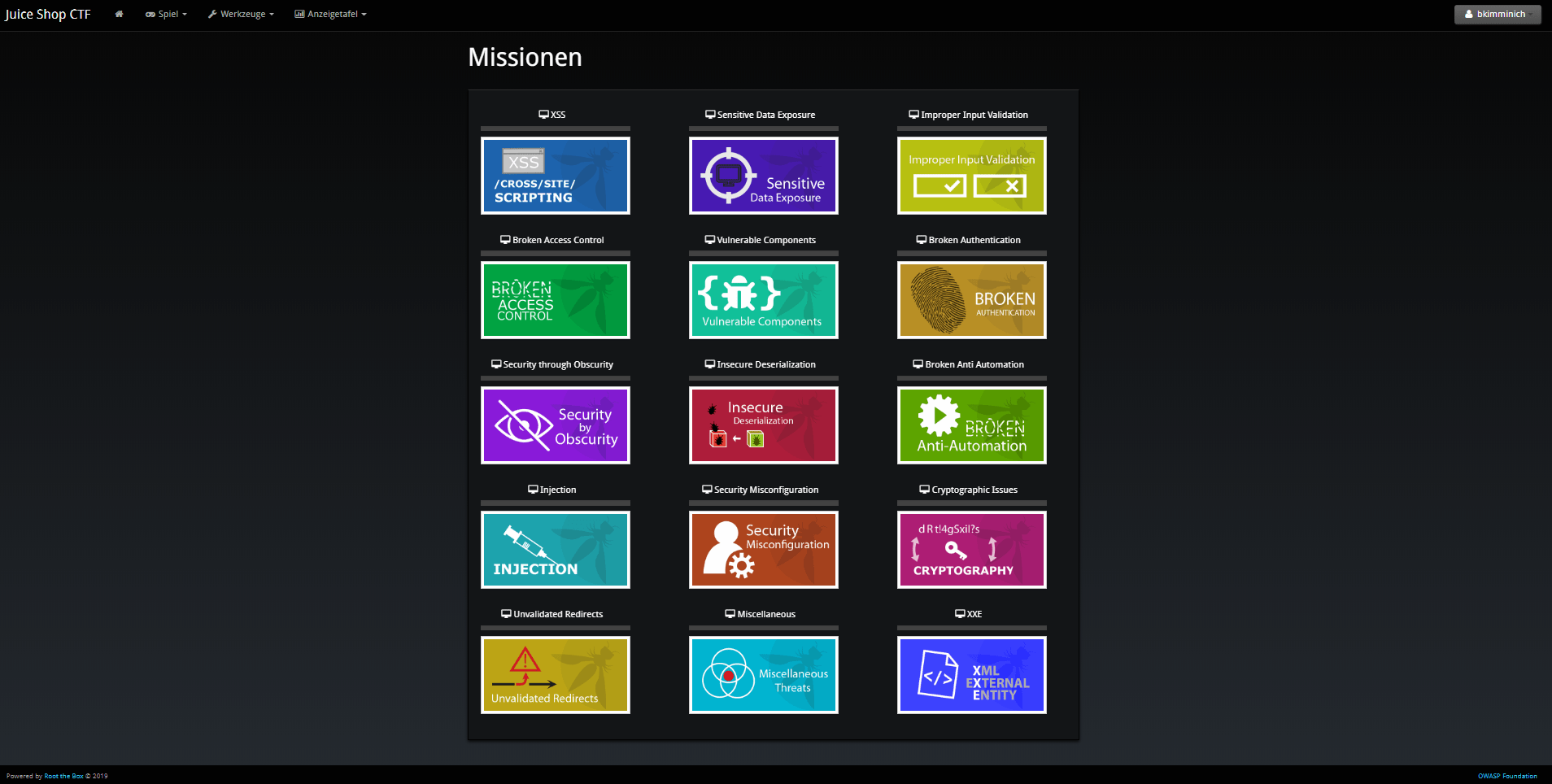
Hacking Challenges
Covering various vulnerabilities and serious design flaws
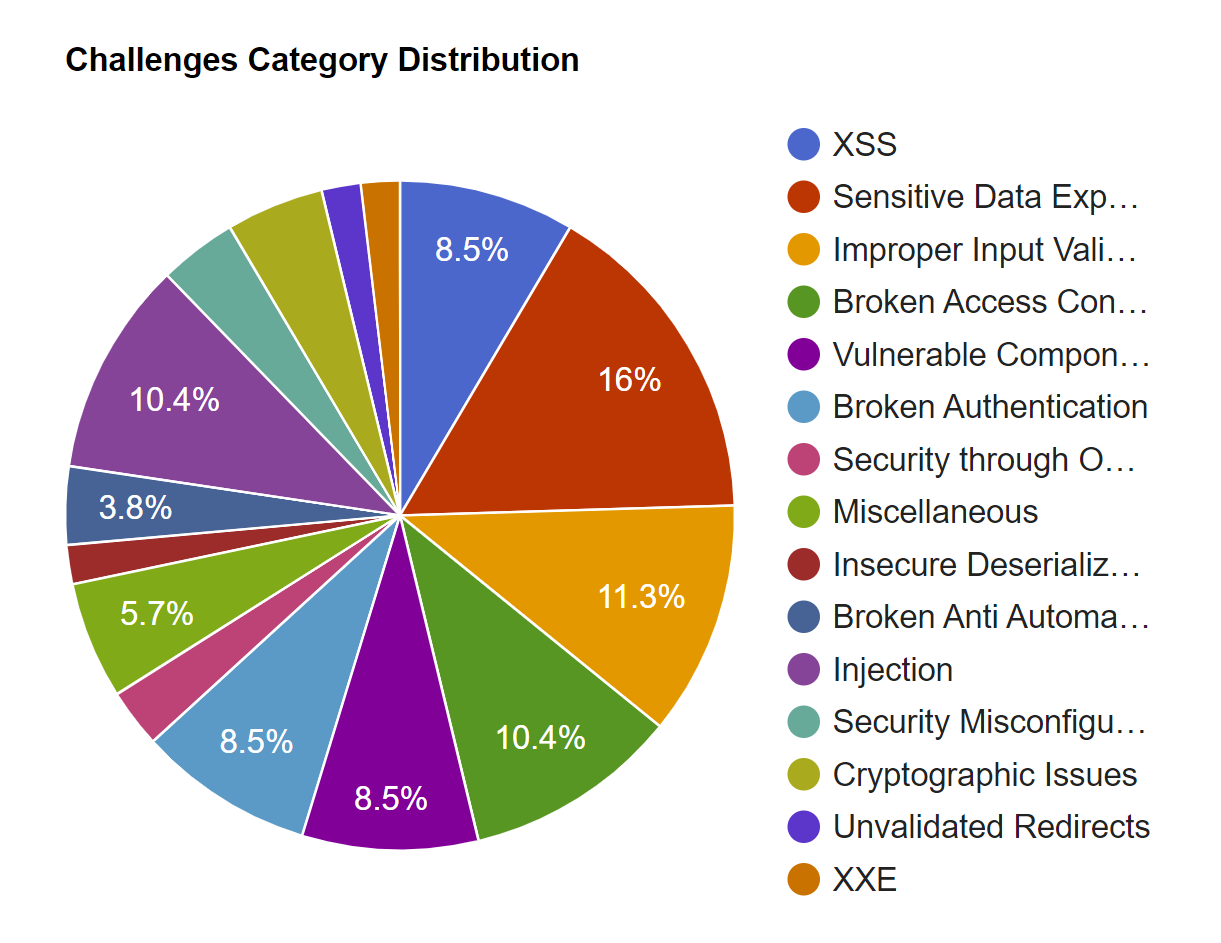
OWASP Juice Shop covers all vulnerabilities from the latest OWASP Top 10 and more.
Challenge Difficulty
There's something to do for beginners and veterans alike

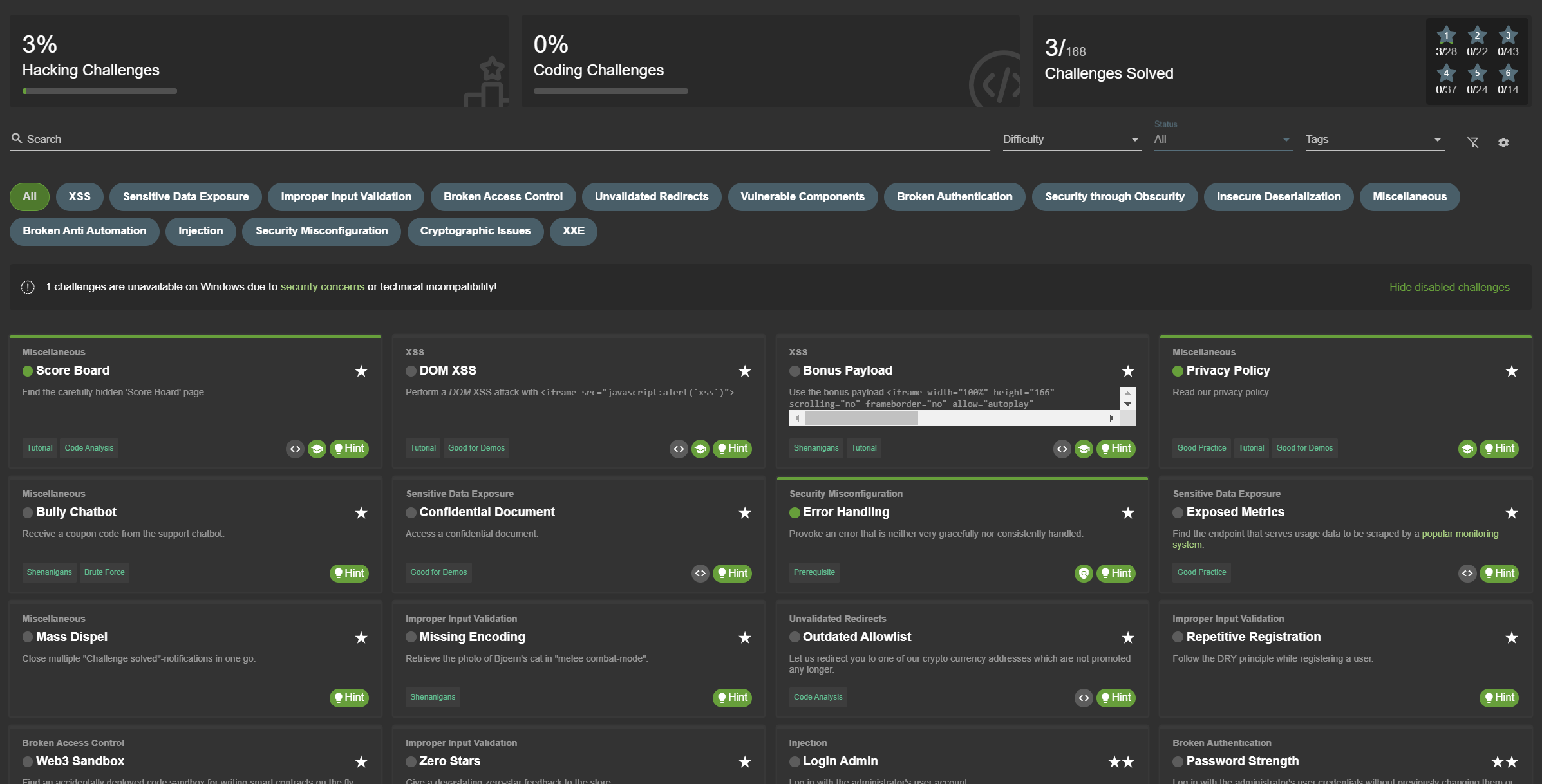
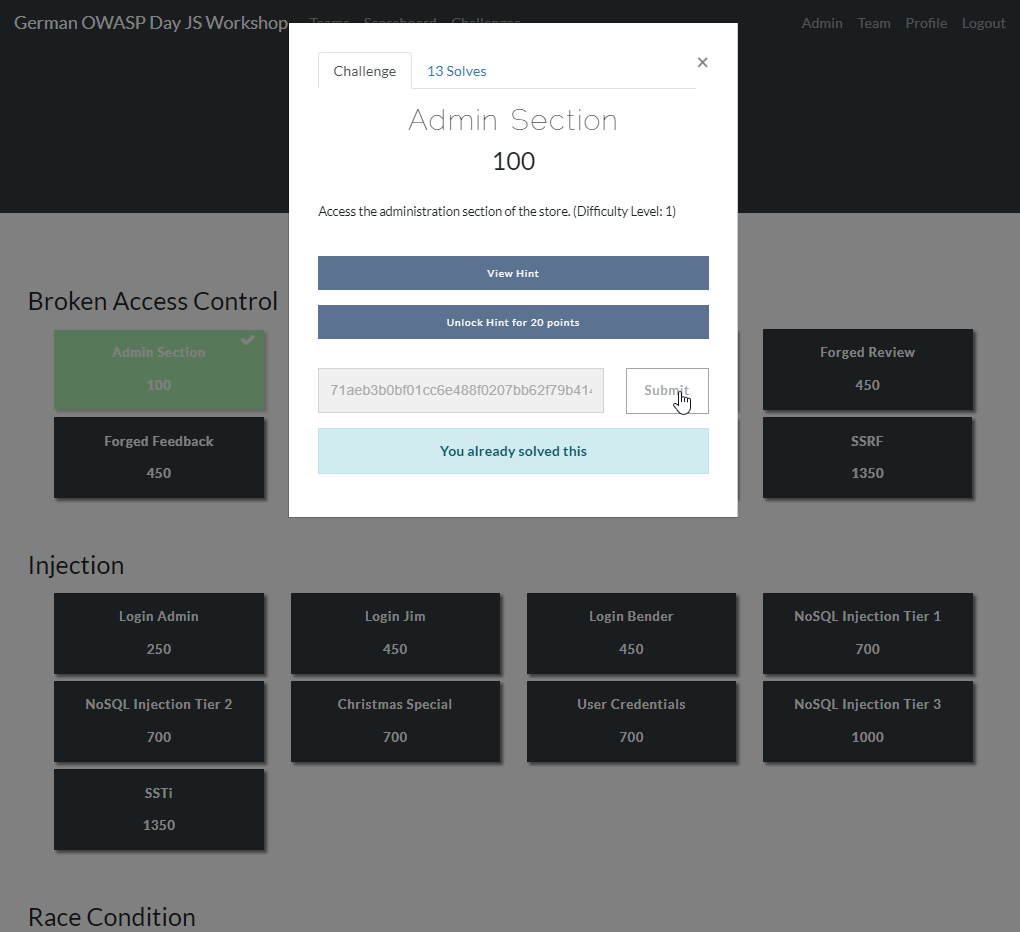
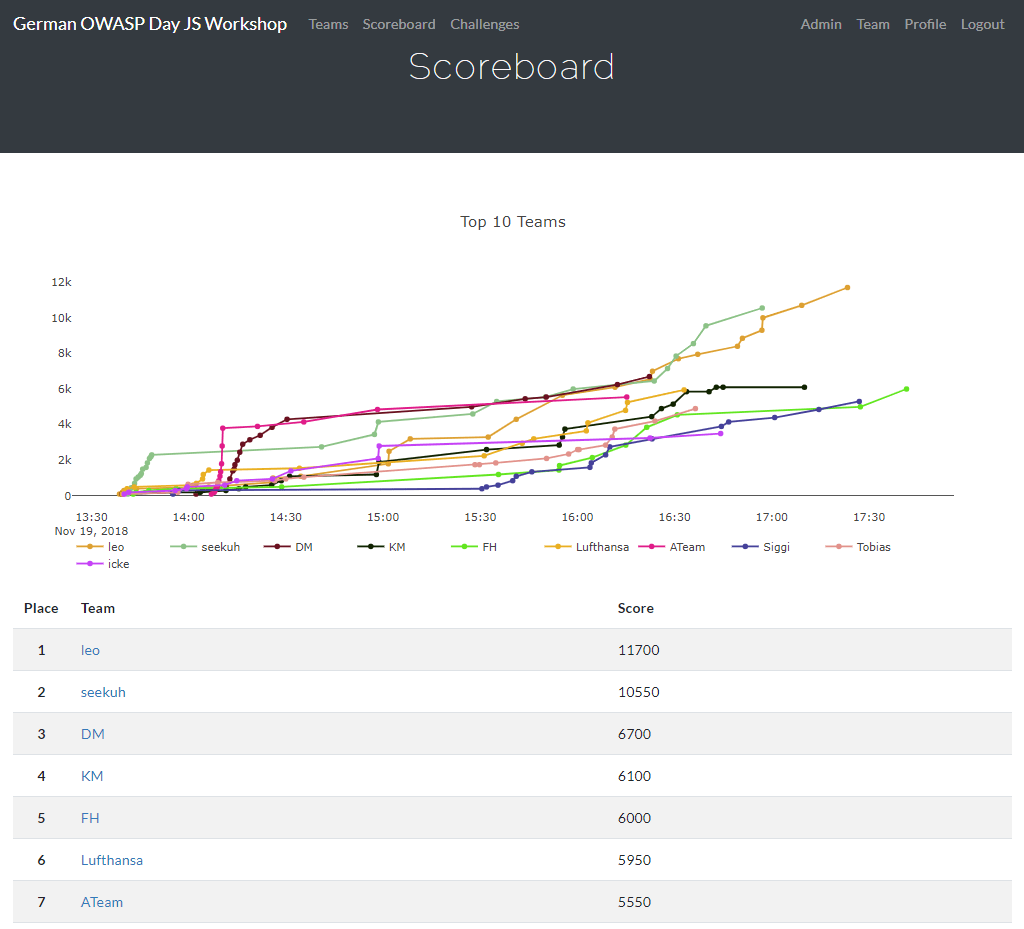
Score Board
Challenge progress is tracked on server-side
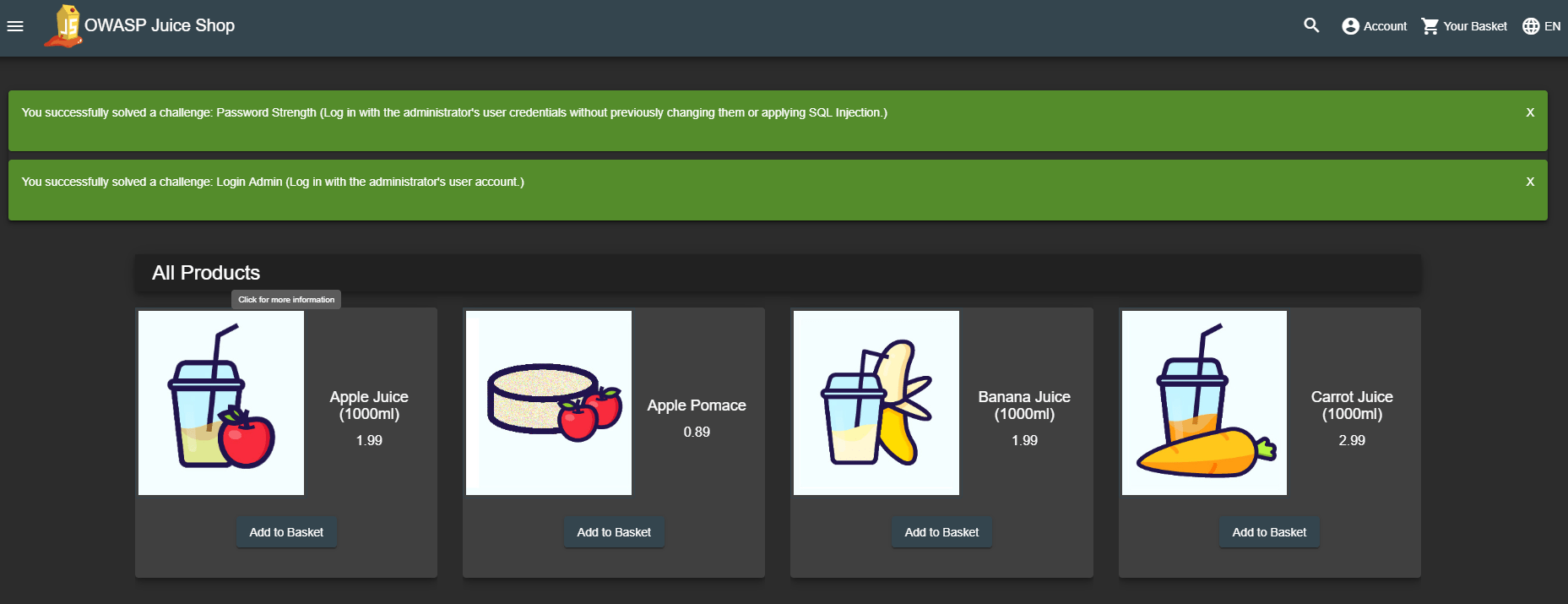
Immediate Feedback
Solved challenges are announced as push notifications
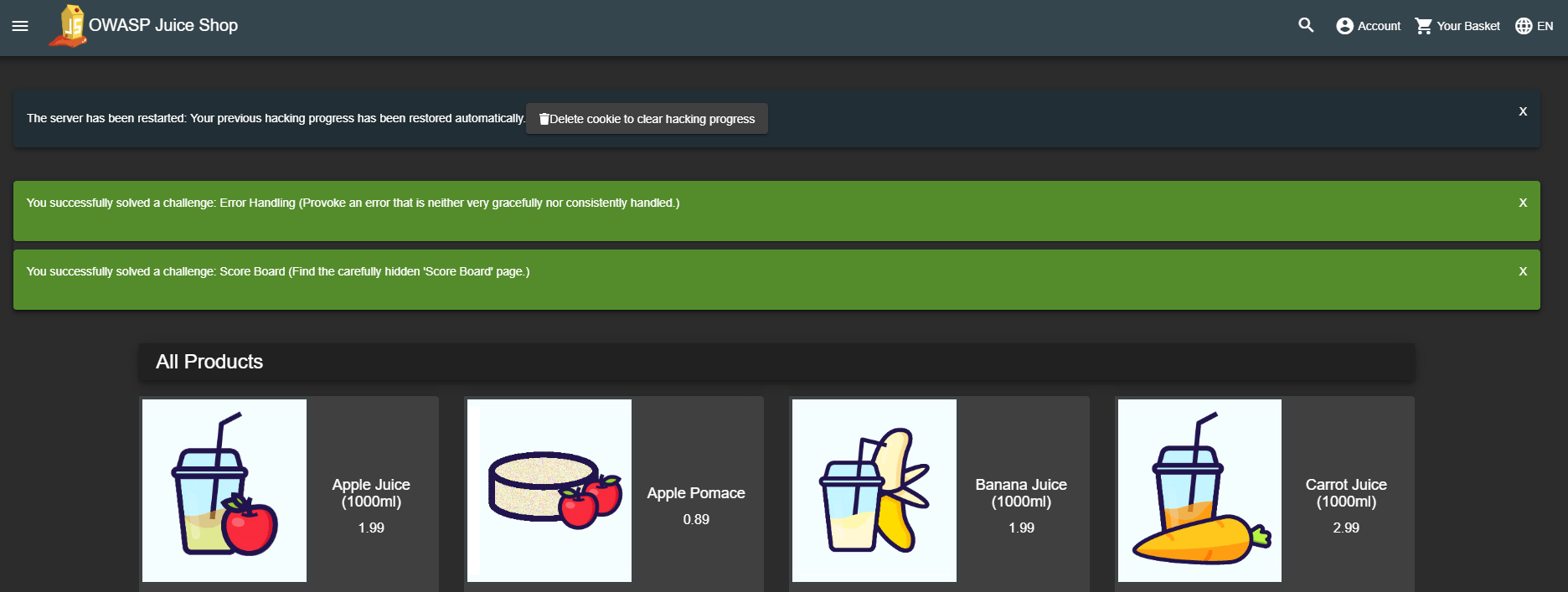
Restore your Progress
Auto-saves your hacking progress and restores on server restart
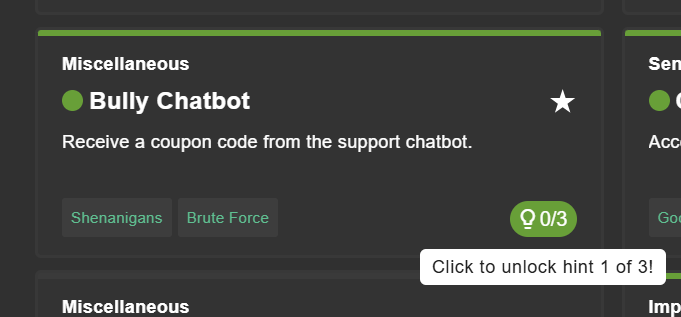
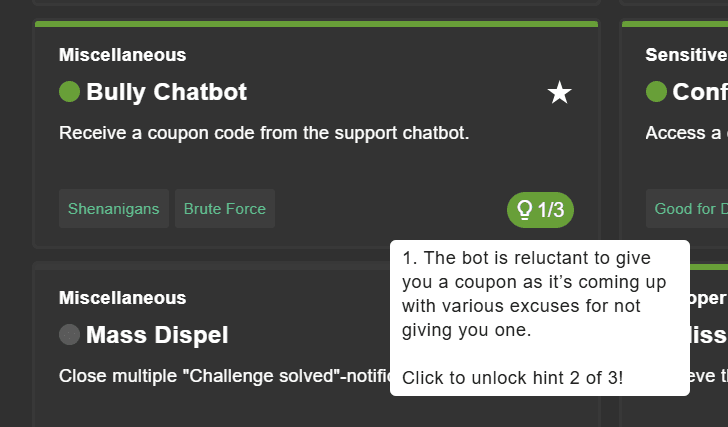
Challenge Hints
All challenges come with one or more unlockable hints
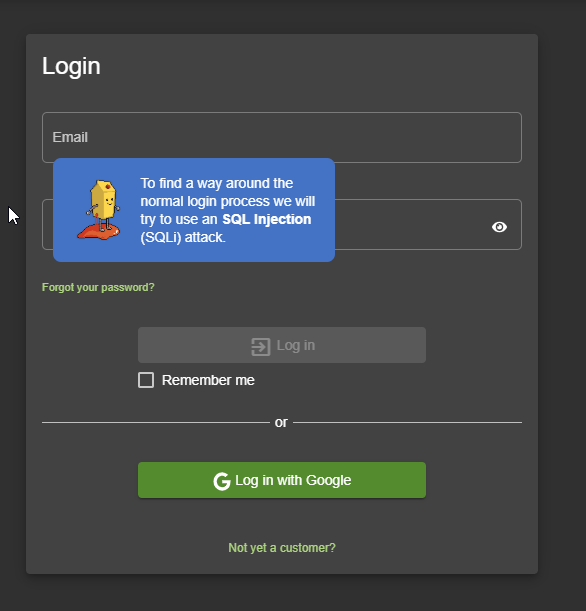
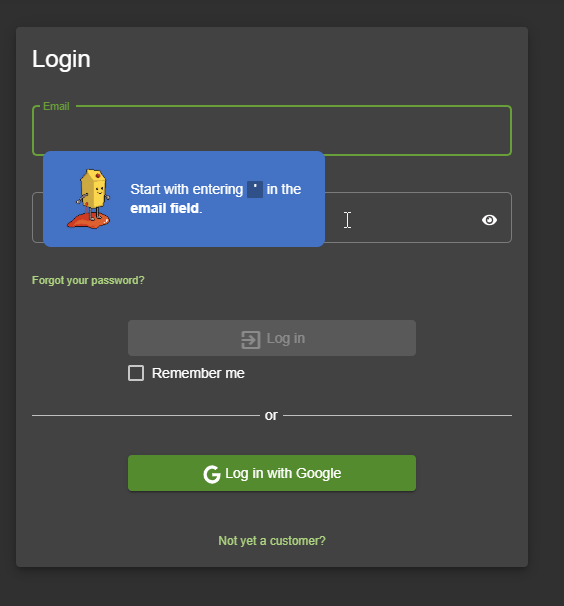
Hacking Instructor
Some challenges come with an embedded interactive tutorial
Tutorial Mode
Gradually unlocking tutorials and the entire Score Board
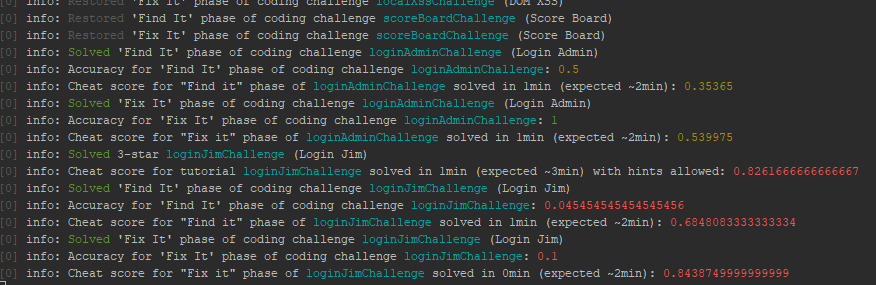
Cheat Detection
Solved challenges are rated based on cheating probability
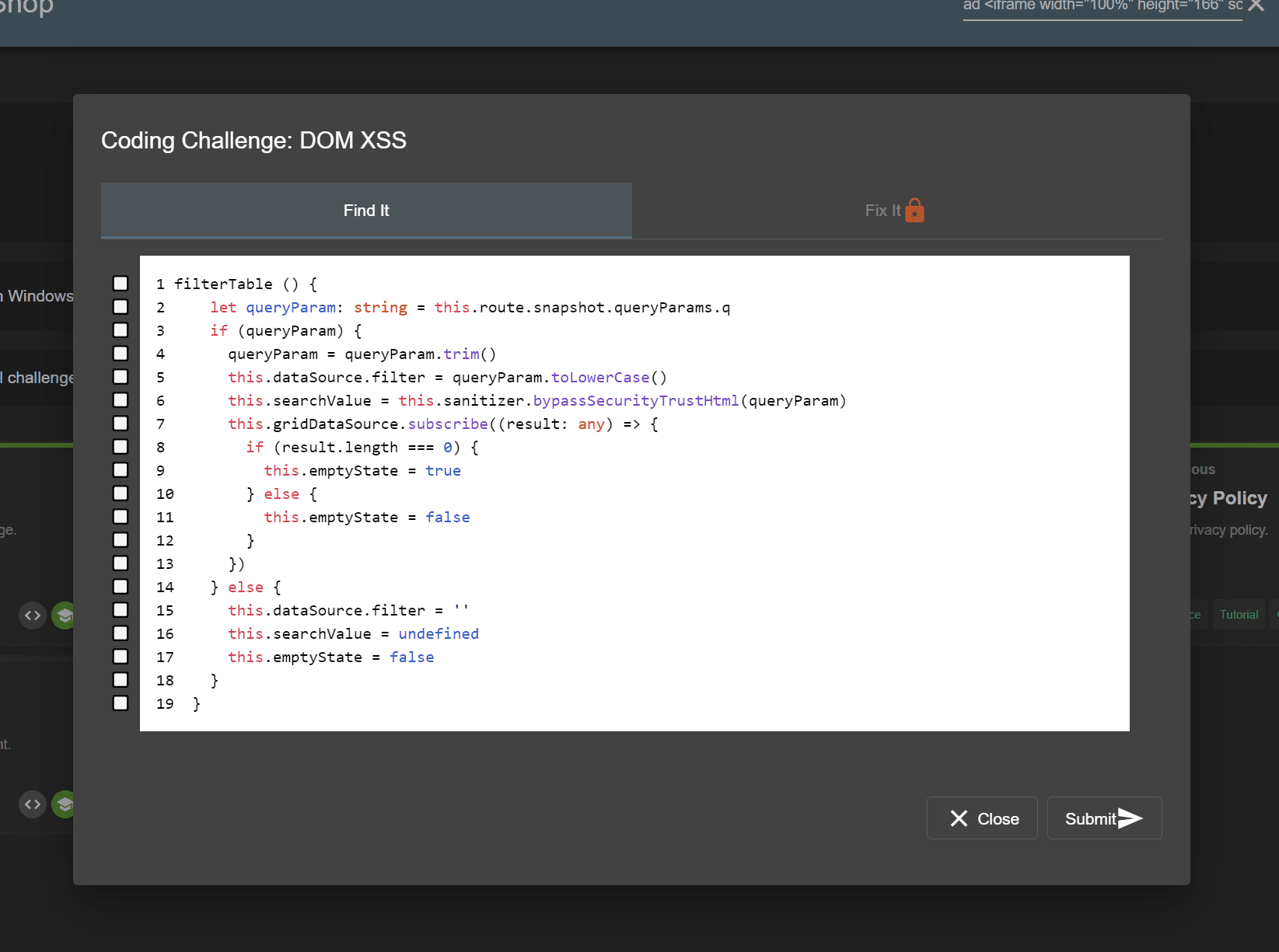
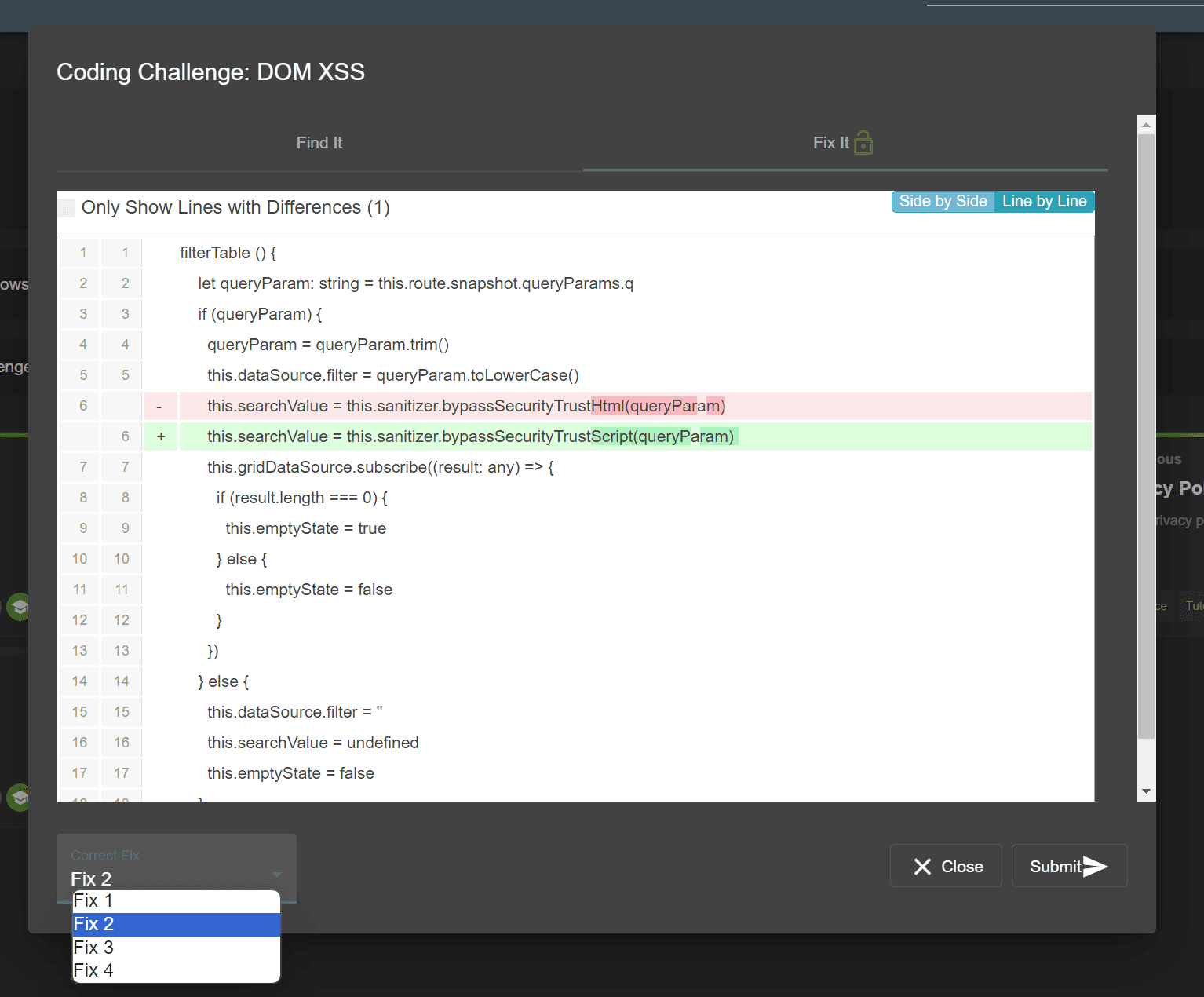
Coding Challenges
Identify the underlying code flaw and select an appropriate fix
Juice Shop is CTF-ready
Flag codes can optionally be displayed for solved challenges
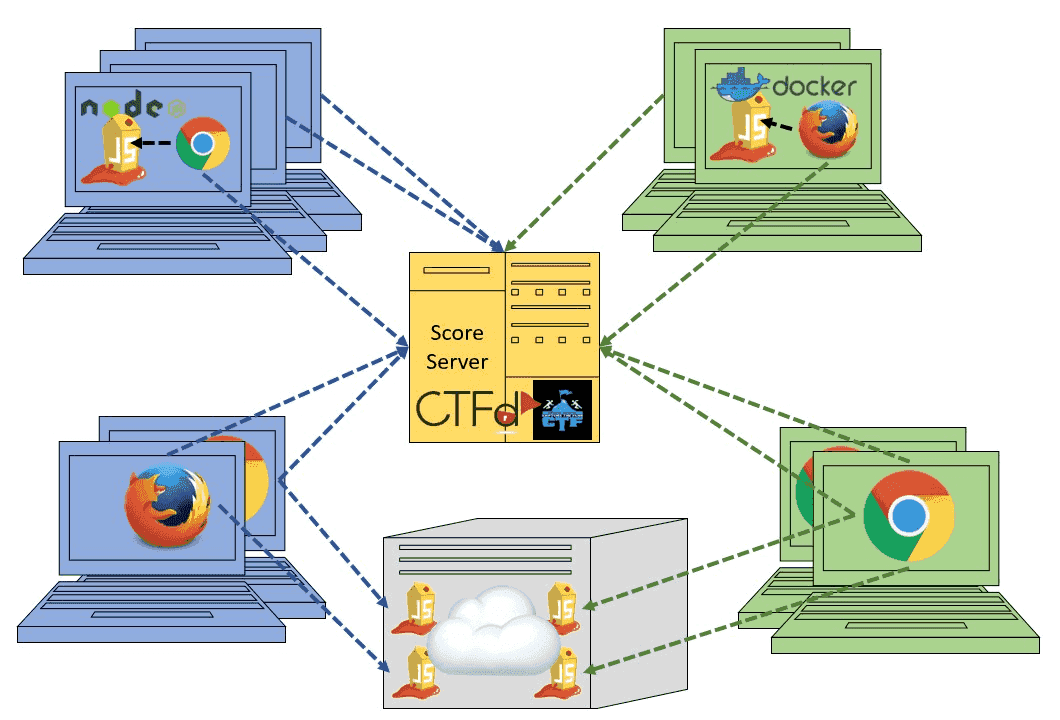
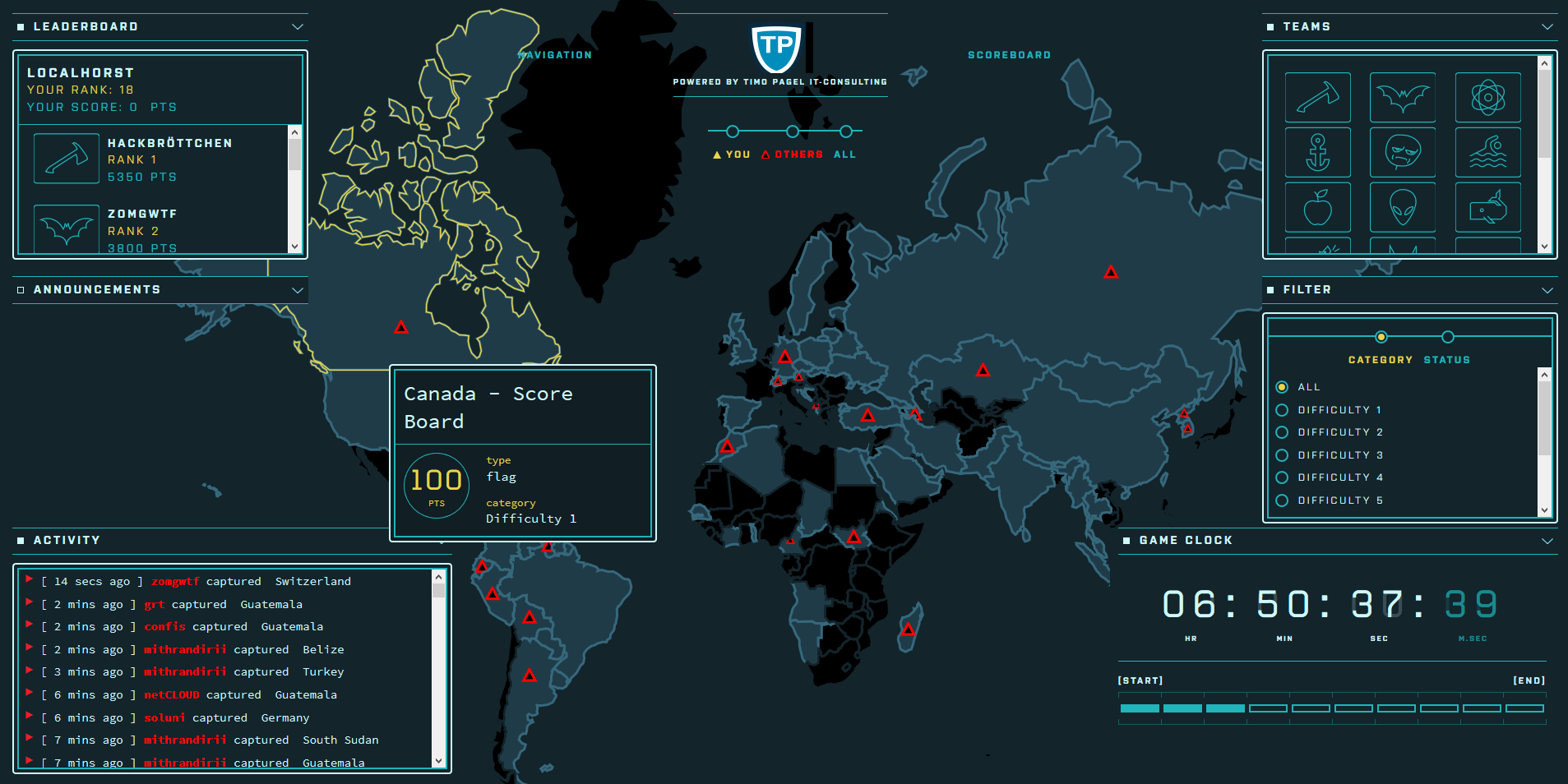
Frictionless CTF-Events
All participants use individual Juice Shop instances anywhere, sharing only the flag code-ctfKey and a central score server.
CTF Extension
Utility project to help you host a hacking event on CTFd, FBCTF or RootTheBox

Simple Installation
Locally via npm i -g juice-shop-ctf-cli or as Docker container


Setup Wizard
Run juice-shop-ctf on the command line and let a wizard create a data-dump to conveniently import into CTFd, FBCTF, or RootTheBox
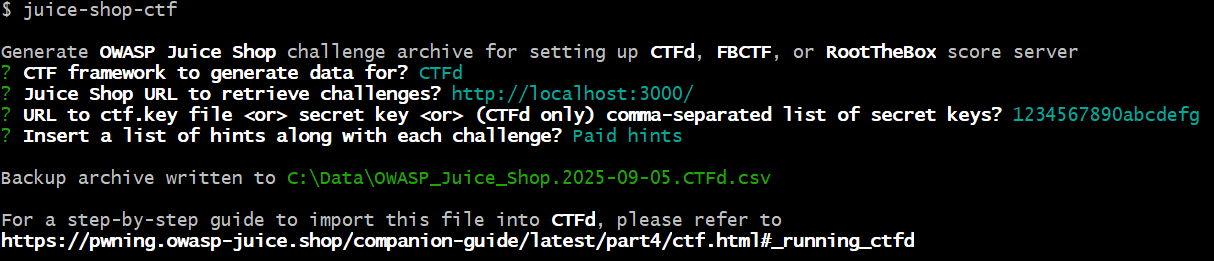
Configuration File Option
Run juice-shop-ctf --config myconfig.yml to use non-interactive mode passing in configuration via YAML file
ctfFramework: CTFd | FBCTF | RootTheBox
juiceShopUrl: http://localhost:3000
ctfKey: https://raw.githubusercontent.com/bkimminich/juice-shop/master/ctf.key
countryMapping: https://raw.githubusercontent.com/juice-shop/juice-shop/master/config/fbctf.yml
insertHints: none | free | paid
Screenshots from CTF games
Your CTF score server instance will be ready-to-play in <5min
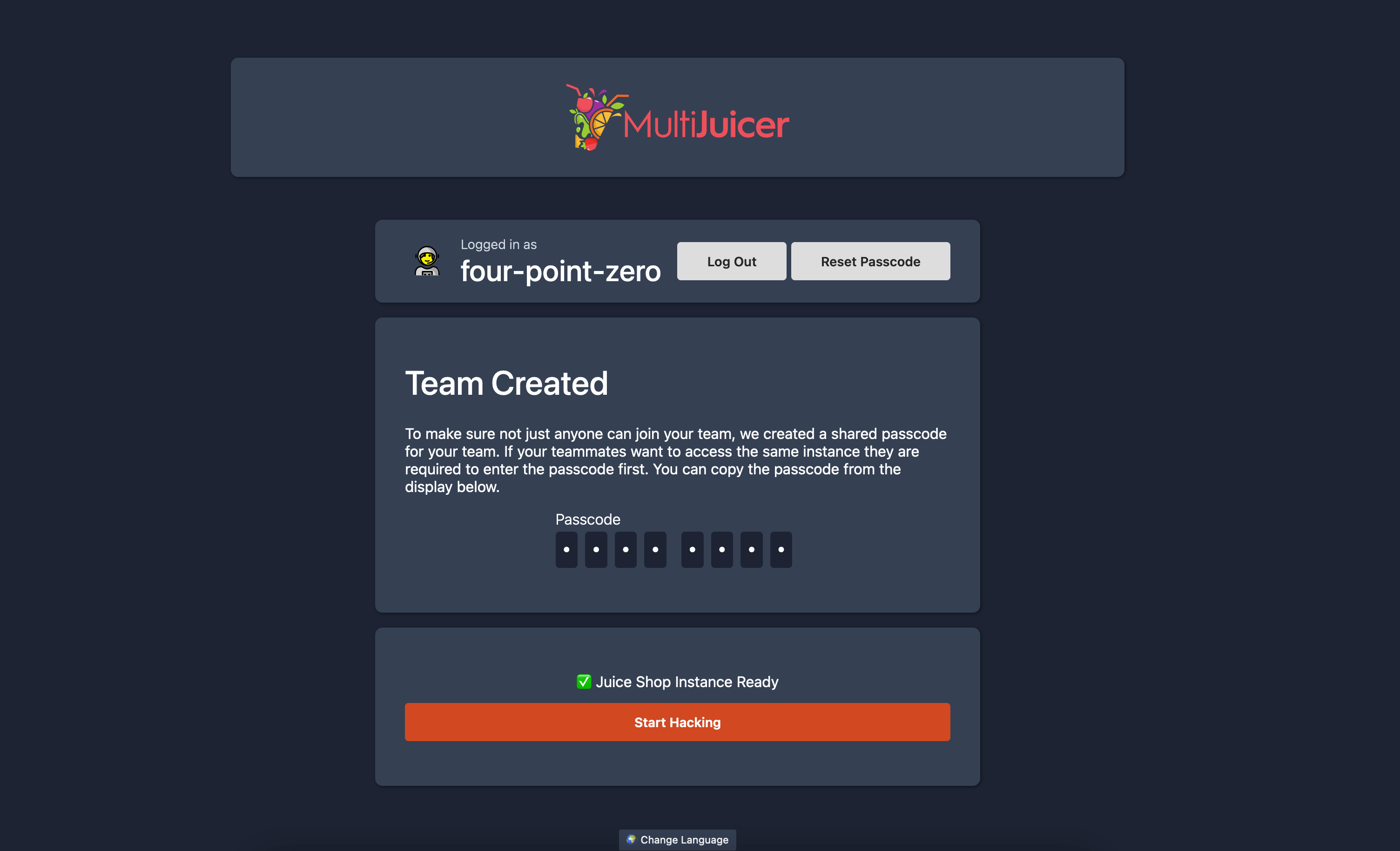
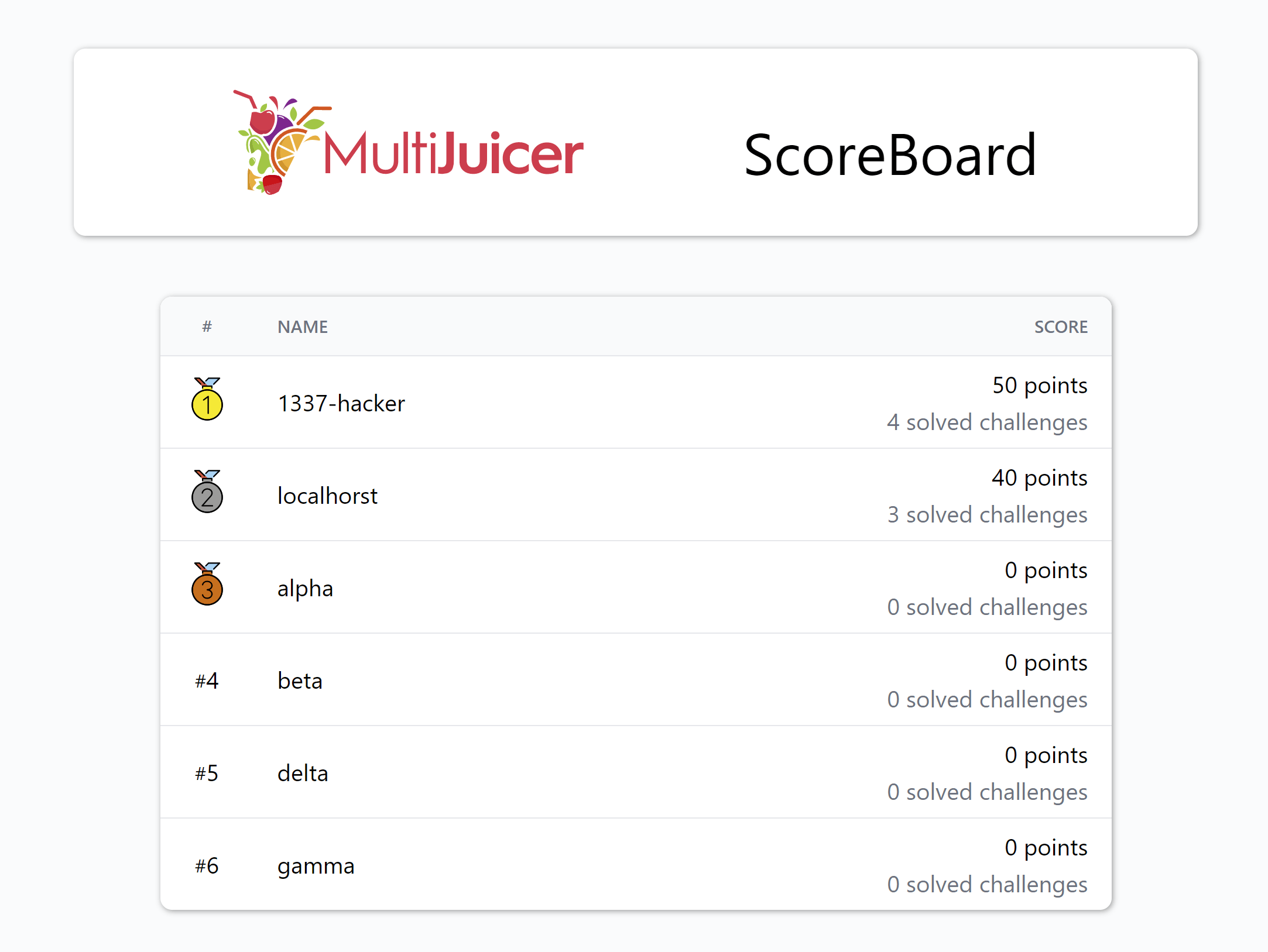
MultiJuicer Platform
Official platform to run separate Juice Shop instances for training or CTF participants on a central Kubernetes cluster

Custom JuiceBalancer
Restricts number of users to team members and protects against illicit cross-team instance access
Simplicity & convenience
Trivial registration, transparent instance stickiness, CTF-friendly score board out-of-the-box, automatic light/dark mode
MultiJuicer-To-Go


 The specifically designed LEGO tower allows bringing a 4x Raspberry Pi cluster with PoE & cooling fans to any training and have MultiJuicer instances running literally out of the box! Also needed: PoE switch, WiFi router, and Internet uplink via cable e.g. through additional WISP router. Build your own with our part list and build manual.
The specifically designed LEGO tower allows bringing a 4x Raspberry Pi cluster with PoE & cooling fans to any training and have MultiJuicer instances running literally out of the box! Also needed: PoE switch, WiFi router, and Internet uplink via cable e.g. through additional WISP router. Build your own with our part list and build manual.
Re-branding
Fully customizable business context and look & feel
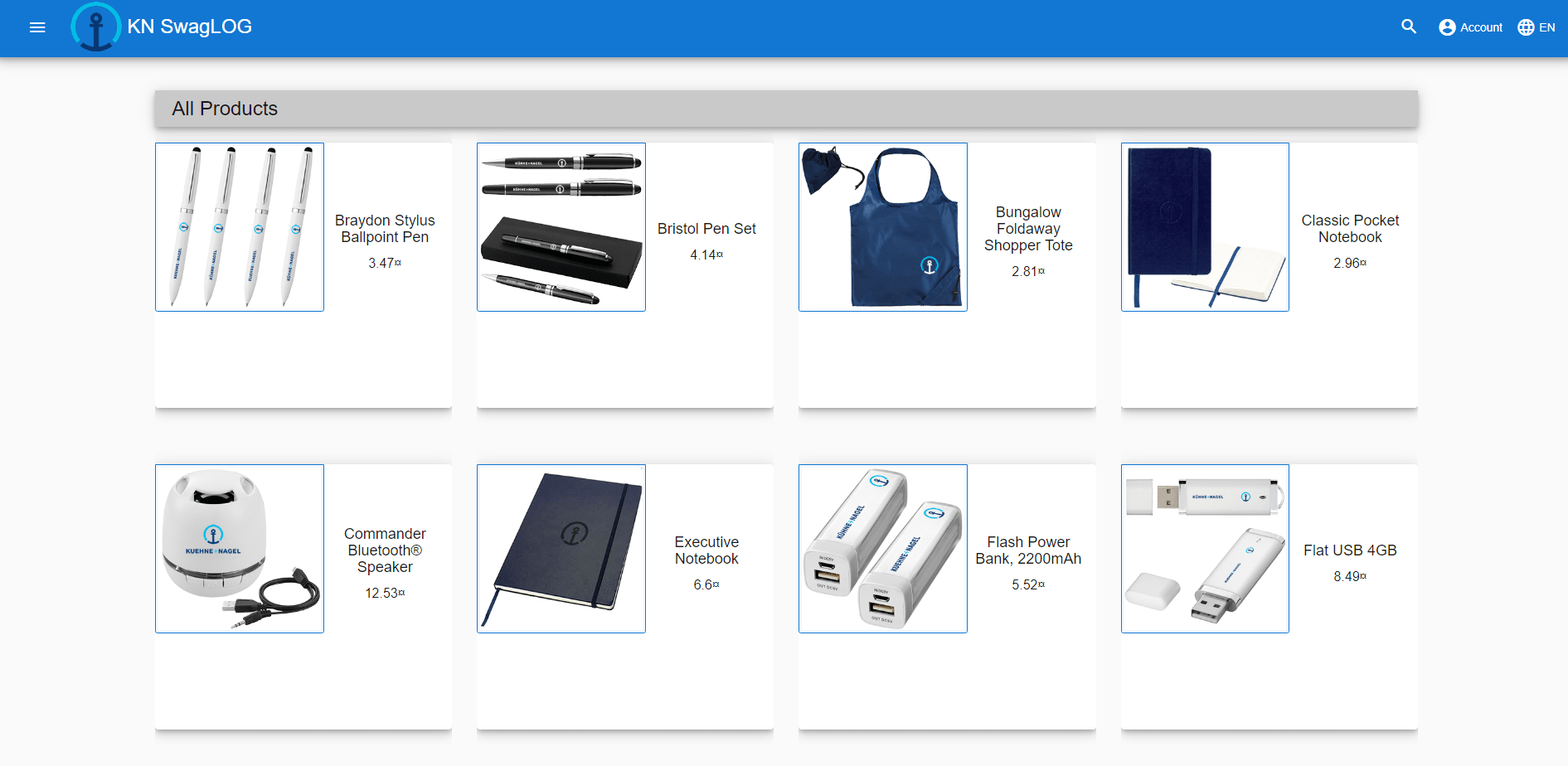
Configurative Customization
Customize the application via a simple YAML file
application:
domain: juice-sh.op
name: 'OWASP Juice Shop'
logo: JuiceShop_Logo.png
favicon: favicon_js.ico
theme: bluegrey-lightgreen
showVersionNumber: true
showGitHubLinks: true
numberOfRandomFakeUsers: 0
altcoinName: Juicycoin
privacyContactEmail: donotreply@owasp-juice.shop
customMetricsPrefix: juiceshop
social:
twitterUrl: 'https://twitter.com/owasp_juiceshop'
facebookUrl: 'https://www.facebook.com/owasp.juiceshop'
[...]
[...]
Choose your own inventory
The YAML configuration allows you to override all products
products:
-
name: 'Product Name'
price: 100
description: 'Product Description'
image: '(https://somewhe.re/)image.png'
useForProductTamperingChallenge: false
useForChristmasChallenge: false
fileForRetrieveBlueprintChallenge: ~
reviews:
- { text: 'Customer review', author: jim }
-
name: 'Product with Lorem Ipsum description, filler image and random price'
Your config is validated on server startup to prevent broken or unsolvable challenges!
Modern Web-Architecture
JavaScript/TypeScript all the way from UI to REST API
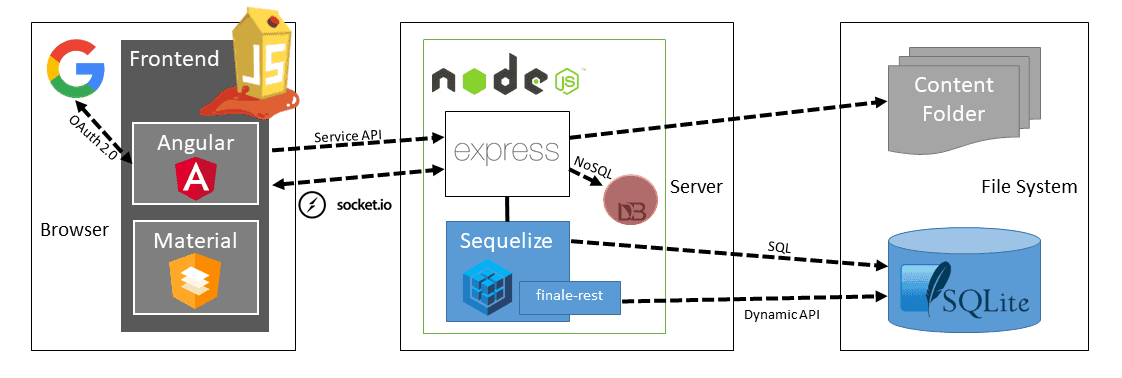
Simple Installation
Comes with cloud, local and containerized run options








Multi-language support
Crowd-sourced UI translations for 40+ languages
Test Pyramid
Maximizing Test Automation & Code Coverage




DevOps Pyramid
Automated Build, CI/CD & Code Analysis










Integration Stacks
Convenient monitoring, notification and data integration capabilities




Solution Webhook
Sends a payload to a specified URL whenever a challenge is solved
{
"solution": {
"challenge": "localXssChallenge",
"hintsAvailable": 2,
"hintsUnlocked": 0,
"cheatScore": 0,
"totalCheatScore": 0.15,
"issuedOn": "2025-09-04T18:24:33.027Z"
},
"ctfFlag": "b0d70dce...b85fac6785dba2349b",
"issuer": {
"hostName": "fv-az116-673",
"os": "Linux (5.4.0-1031-azure)",
"appName": "OWASP Juice Shop",
"config": "default",
"version": "19.0.0"
}
} Grafana Dashboard
JSON template allows to import a dashboard into Grafana consuming and displaying all metrics gathered via Prometheus
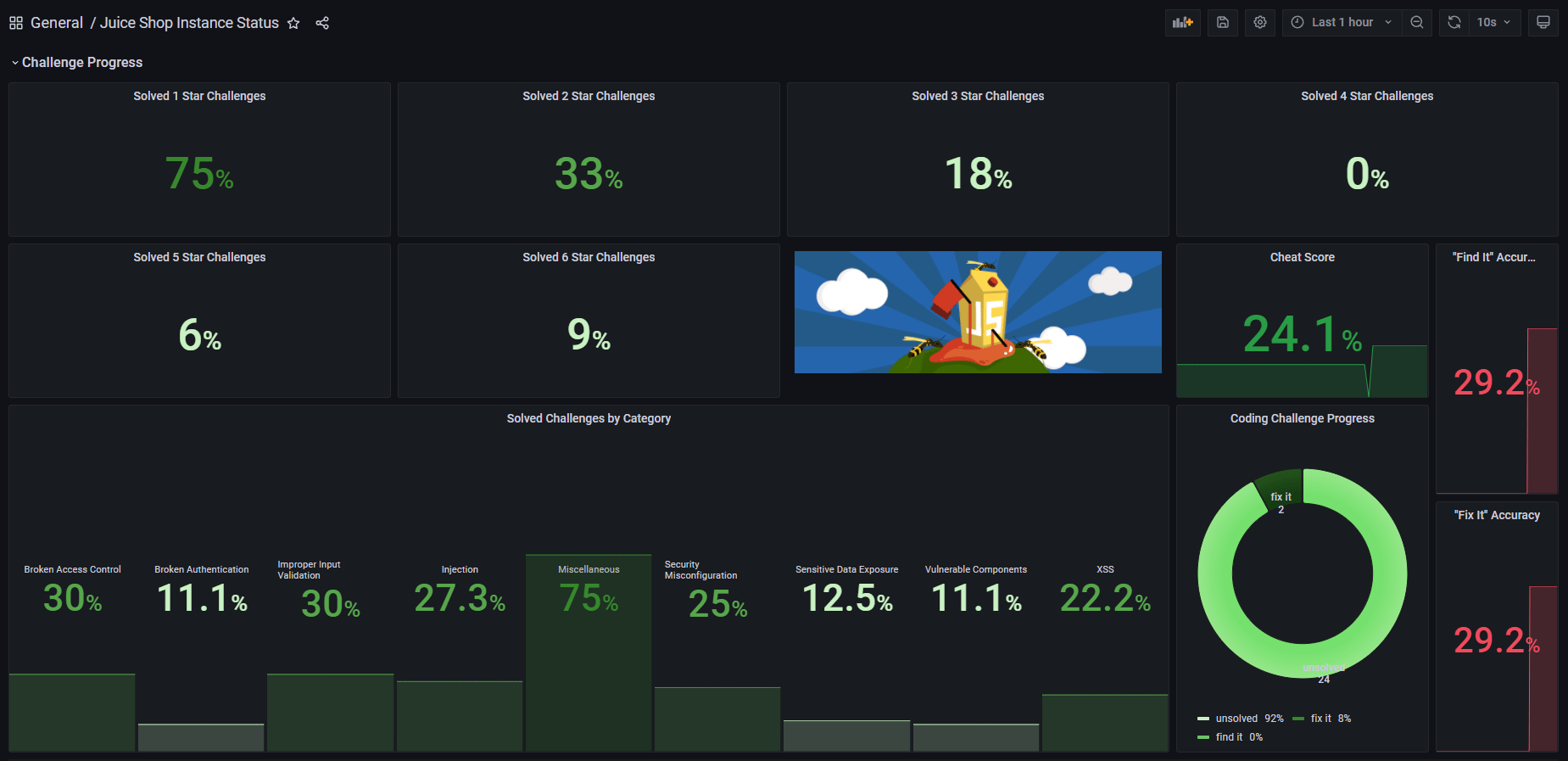
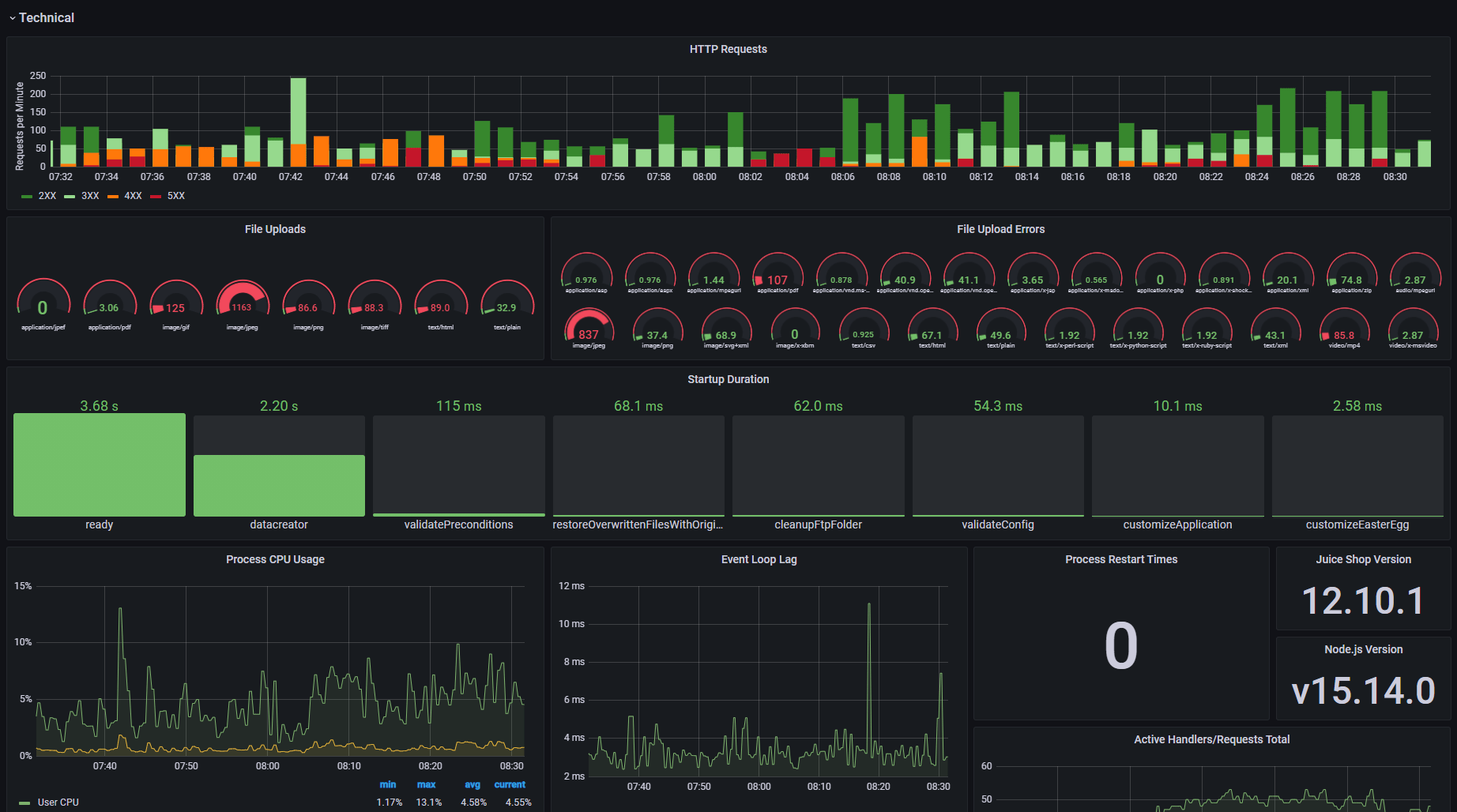
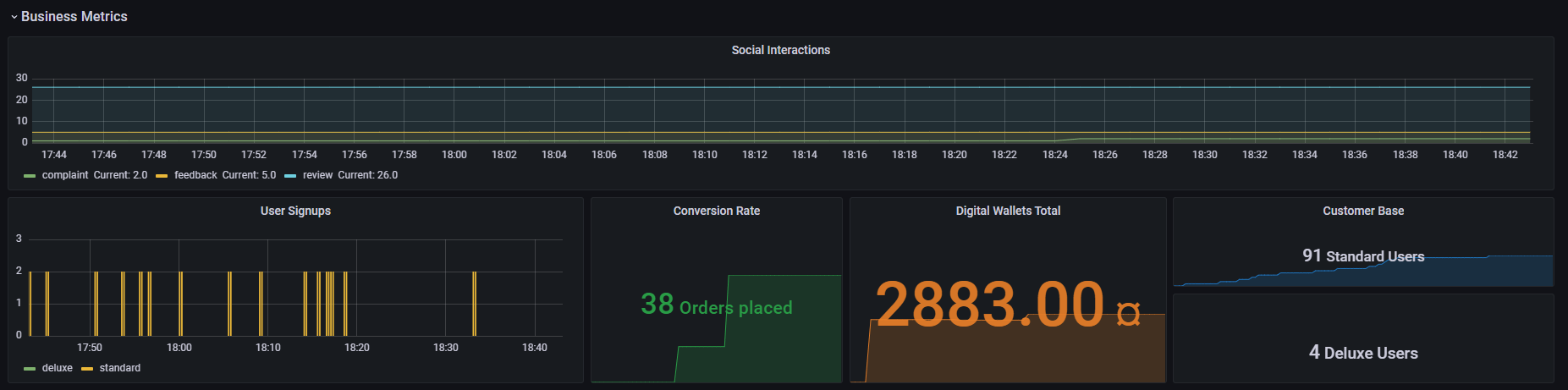
FAQ
- Can I use my Pentesting toys?
- Can I do a white box pentest?
- Can I use the internet?
- Installation does not work!
- What if I crash the server?
- I'm stuck with a challenge!
- I found another vulnerability!
- Why are some challenges disabled?
- Can I contribute to the project?
- This project really needs a jingle!
If FAQ & README don't help, ask for help in the chat. Please refrain from using GitHub issues for support requests.
Can I use my Pentesting toys?
Yes, definitely! Use whatever pentesting tools you like the most!

Proxies like Zed Attack Proxy or BurpSuite Free Edition can definitely be useful. Automatic tools like Arachni or Nikto might find some vulnerabilities but will obviously not be able to get the Score Board to 100% for you.
Can I do a white box pentest?
No! The code from GitHub would spoiler all challenge solutions!

You can of course use everything that the application hands to you in the browser, so use its DevTools! Peeking into the code snippets provided on the Score Board is fine, too. If you are a SAST tool vendor, you can obviously test your scanner against the Juice Shop codebase!
Can I use the internet?
Yes! Feel free to look for ideas, clues & hints everywhere!

Again: Except for the application's own GitHub repository! Also there are many third party solution guides and videos available online, so you might want to be careful about accidental spoilers.
Installation does not work!
Please carefully follow the instructions in the README!

If Setup & Troubleshooting docs don't help, you can always ask the community or open an issue!
What if I crash the server?
The application is cleanly reset on every startup!

Your Score Board progress is saved automatically and will restore after server restart! This only works if cookies are enabled in your browser.
I'm stuck with a challenge!
Find more hints in the free official companion guide on Leanpub


The eBook can also be read online. You can always ask for hints in the community chat as well!
I found another vulnerability!
Please report untracked vulnerabilities by opening an issue
Of course you can also contribute directly by opening a pull request. Just stick to the contribution guide!
Why are some challenges disabled?
Some challenges are actually harmful in containerized or public cloud environments and are deliberately disabled there



This affects all Stored XSS due to risk of abuse, all XXE challenges (because they can lead to instance death by segfault error) and the SSTi, Deserialization and some NoSQLi challenges (as they could have unforeseeable side effects on the hosting platform).
Can I contribute to the project?
Of course! Visit our backlog on GitHub & translations on Crowdin


Issues labelled with good first issue and/or help wanted are the best starting point!
This project really needs a jingle!
We fully agree! Thankfully, Brian Johnson already recorded one!
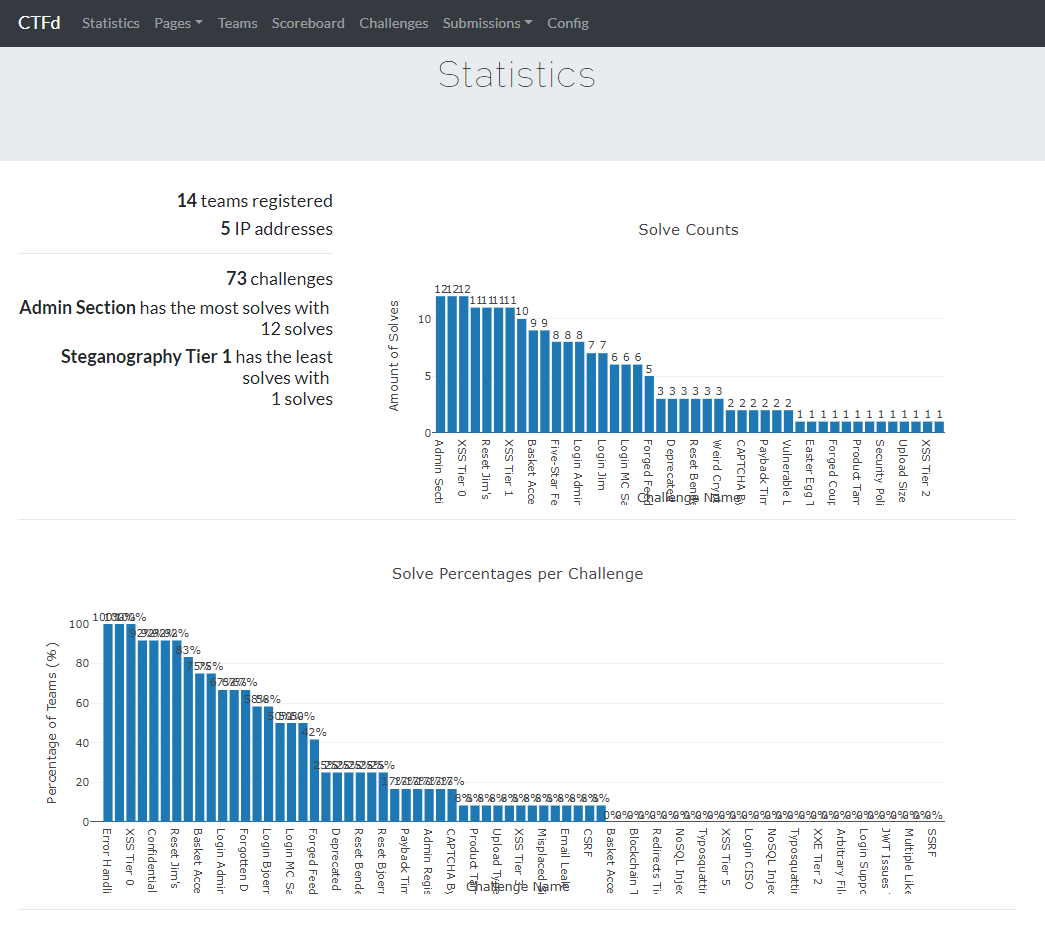
Juice Shop Success Pyramid™
Some amazing facts & stats about the project








Project Roadmap
Additional Information
$ zip -r -q -9 postcard intro



Copyright (c) 2014-2025 Björn Kimminich / @bkimminich
Licensed under the MIT license.
Created with reveal.js - The HTML Presentation Framework



